-
Type:
Bug
-
Resolution: Done
-
Priority:
Medium
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49
-
Platform
-
All
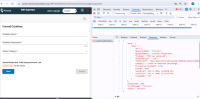
An internal URL (such as an internal API endpoint, internal admin page, or server details) is being disclosed to unauthorized users. This information could be used by malicious actors to gain insights into the infrastructure or attack the system further.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Internal URL Disclosure | https://uatamrit.piramalswasthya.org:8084/OpenKM/Download?uid= | CWE-200: | 5.2 | Medium | OWASP Configuration and Deploy Management Testing | The application revealed internal server paths or URLs in its responses when files were accessed. This information disclosure could provide attackers with insights into the server structure, aiding in further attacks such as directory traversal, local file inclusion, or targeted file access. | Exposure of internal directory structures assists attackers in crafting more precise and damaging attacks. Information leakage lowers the overall security posture and can lead to exploitation of underlying system vulnerabilities |
Mask or sanitize internal paths in responses to avoid disclosing server or directory information. Handle errors and file references in a generic manner without revealing server structure. Implement strict access controls on files and audit file handling endpoints regularly. |
https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure | Step 1: During the security assessment, when accessing a file after uploading, it was observed that the server response disclosed the internal URL or file path. |
- is blocked by
-
AMM-1924 Unauthenticated File Access Allows Exposure of Sensitive Files
-
- Closed
-