-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49, AMRIT Sprint 50, AMRIT Sprint 51, AMRIT Sprint 52, AMRIT Sprint 53, Sprint 54
-
Platform
-
UAT
The application issues JSON Web Tokens (JWTs) that do not expire correctly or have an excessively long expiration time. This can allow an attacker to reuse stolen or leaked tokens for unauthorized access long after they should have expired.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Improper JWT Expiration | https://uatamrit.piramalswasthya.org/common-api/cti/getloginkey | CWE-613 | 5.3 | Medium | OWASP Session Management Testing | This means that if an attacker compromises a JWT token—for example via XSS, interception, or leakage—they can reuse it for over 8 hours without interruption. If the user forgets to log out or the token is stolen by malware or a network attacker, the attacker gets persistent access to user data and actions for an extended period, increasing the risk of session hijacking, unauthorized activity, and privilege misuse. | JWT tokens valid for 8+ hours severely increase the attack window for replay attacks, session hijacking, and data breaches. Automated credential and token theft tools can exploit long-validity tokens to maintain unauthorized access throughout a work shift or overnight, bypassing reauthentication controls. |
Reduce access token lifetimes to 15–30 minutes for critical APIs; use refresh token flow for seamless user experience. Enforce automatic token renewal, idle timeouts, and mandatory logout after risk events (e.g., IP change, privilege escalation). |
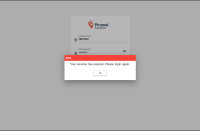
https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/06-Session_Management_Testing/10-Testing_JSON_Web_Tokens | Step 1: During the security assessment, a random API request was captured and its JWT token was analyzed using JWT tool extensions in Burp Suite. It was found that the token’s expiration (exp) time was set for longer than 8 hours. |