-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49, AMRIT Sprint 50
-
Platform
-
UAT
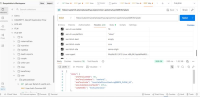
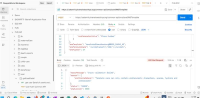
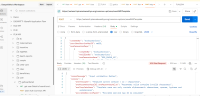
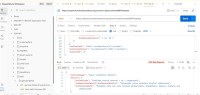
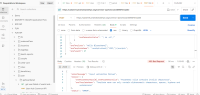
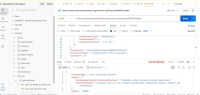
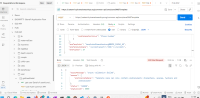
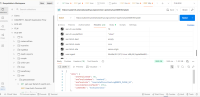
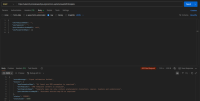
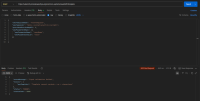
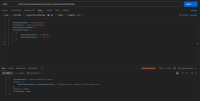
The application does not properly validate user-supplied input in https://uatamrit.piramalswasthya.org/ecd/supervisor/innerpage-supervisor?data=smsTemplate. Improper input validation can lead to security issues such as SQL injection, XSS (Cross-Site Scripting), command injection, or application crashes.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Improper Input Validation | https://uatamrit.piramalswasthya.org/ecd/supervisor/innerpage-supervisor?data=smsTemplate | CWE-79 | 5.4 | Medium | OWASP Client Side Testing | Allowing raw HTML input without proper validation increases the risk of future client-side vulnerabilities like stored XSS or UI manipulation |
||||
| Weak input validation may allow chaining with other attacks. | Implement server-side validation to restrict HTML tags and unexpected input types. Sanitize all incoming user data using a secure whitelist approach. |
https://cheatsheetseries.owasp.org/cheatsheets/Input_Validation_Cheat_Sheet.html |