-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49
-
Platform
-
UAT
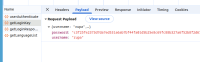
The application is handling user credentials (username and/or password) in plain text, either during storage or transmission. This poses a significant security risk, as attackers could intercept or access credentials, leading to account compromise or unauthorized access.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Username And Password In Plain text | https://uatamrit.piramalswasthya.org/common-api/cti/getloginkey | CWE-319 | 6.1 | Medium | OWASP Authentication Testing | This means that anyone able to intercept traffic between the client and the API (for example, on public Wi-Fi or through a compromised local network) could instantly recover actual usernames and passwords by sniffing network packets. Attackers can leverage this exposure to access user accounts, cause massive data breaches, and further automate attacks against critical business systems if credentials are reused. | Immediate credential theft for any user interacting with the API over insecure channels. | Use strong encryption mechanisms for credentials in transit and storage, and move towards token-based authentication where possible. | https://owasp.org/www-community/vulnerabilities/Password_Plaintext_Storage | Step 1: During the security assessment, the login API request was captured in Burp Suite. It was clearly observed that both the username and password fields were present in the request body and transmitted in plain text format without encryption. |