-
Type:
Bug
-
Resolution: Done
-
Priority:
Medium
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49, AMRIT Sprint 50
-
Platform
-
UAT
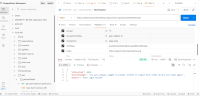
An Insecure HTTP Method vulnerability was discovered in https://uatamrit.piramalswasthya.org/aam/#/login . The application or server accepts unsafe HTTP methods such as PUT, DELETE, TRACE, OPTIONS, or CONNECT, which may allow unauthorized users to modify, delete, or probe resources.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Insecure HTTP Method | https://uatamrit.piramalswasthya.org/aam/#/login | CWE-942 | 3.7 | Low | OWASP Configuration and Deploy Management Testing | While OPTIONS is a standard method, its enablement without strict controls can expose information that assists attackers in planning further attacks. Misconfigured OPTIONS responses might leak sensitive endpoints or allow Cross-Origin Resource Sharing (CORS) misconfigurations to be exploited. | Disclosure of server-supported HTTP methods aiding attackers in reconnaissance. Increased risk of CORS-related vulnerabilities if preflight requests are allowed without proper validation. |
Restrict OPTIONS method responses to only necessary origins and headers. Implement proper CORS policies validating origins and methods. |
https://cwe.mitre.org/data/definitions/942.html | Step 1: During the security assessment, it was observed that the OPTIONS HTTP method was enabled on the server. |