-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49
-
Platform
-
UAT
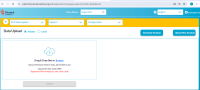
An Unrestricted File Upload vulnerability was discovered in the https://uatamrit.piramalswasthya.org/ecd/supervisor/innerpage-supervisor?data=smsTemplate. The application does not properly validate or restrict uploaded files, allowing an attacker to upload arbitrary files such as scripts or executables. This can lead to remote code execution, data compromise, or defacement of the system.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| Unrestricted File Upload | https://uatamrit.piramalswasthya.org/ecd/supervisor/innerpage-supervisor?data=smsTemplate | CWE-89 | 8.1 | High | OWASP Data Validation Testing | This indicates that the application’s file upload mechanism is vulnerable to file extension manipulation allowing malicious files to bypass validation and be uploaded by disguising them with allowed extensions. | The server-side validation only checks the file extension superficially and does not verify the actual content or enforce strict MIME-type checks. This allows an attacker to upload potentially harmful files disguised with harmless extensions.Malicious SVG files containing embedded scripts can be uploaded and later executed by users, causing stored Cross-Site Scripting (XSS) attacks. Potential server-side vulnerabilities like remote code execution or denial-of-service attacks if malicious files are executed or processed insecurely. |
Perform strict server-side validation by checking file MIME types and content signatures rather than relying solely on file extensions. Sanitize, filter, or convert potentially dangerous file types before processing or serving. Consider allowing only a whitelist of safe extensions and converting files like SVGs to a safe raster format to prevent script execution. |
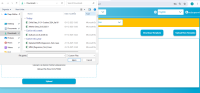
https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload | Step 1: During the security assessment, a malicious SVG file was renamed with the .xlsx extension and uploaded successfully via the file upload functionality. After capturing the upload request in Burp Suite, the file extension was changed back to .svg in the request, and the file was uploaded successfully without any server-side validation preventing the extension manipulation. |