-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49
-
Platform
-
UAT
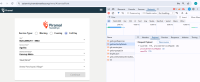
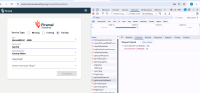
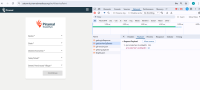
During the VAPT assessment, an IDOR vulnerability was identified in the application. This issue allows an authenticated user to access or modify resources belonging to other users by manipulating a direct object reference (e.g., user ID, order ID) in the request.
| Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| IDOR | https://uatamrit.piramalswasthya.org/tm-api/getUserVanSpDetails https://uatamrit.piramalswasthya.org/mmu-api/location/getLocDetailsBasedOnSpIDAndPsmID |
CWE-284 | 7.5 | High | OWASP Authorization Testing | This demonstrates a lack of proper access control and immediate authorization checks on the API endpoint, allowing an attacker to manipulate parameters and access other users' sensitive information. | Unauthorized data disclosure: Attackers can retrieve details for any user by simply changing the user ID in the request. Data confidentiality is compromised, leading to privacy violations and potential regulatory issues. Attackers could perform further privilege escalation or data tampering. |
Enforce backend access control checks that verify the logged-in user's permissions and ensure they can only access their own data. Validate all input parameters on the server side to prevent IDOR (Insecure Direct Object Reference) attacks. implement proper access controls and implement role-based access control (RBAC). |
https://cheatsheetseries.owasp.org/cheatsheets/Insecure_Direct_Object_Reference_Prevention_Cheat_Sheet.html | Step 1: During the security assessment, it was observed that the endpoint getUserVanSSpDetails could be accessed with a modified user_id parameter (changing from 536 to 535) in a request that was originally meant for an authenticated user. The server responded with details for the other user without requiring re-authentication. |