-
Type:
Bug
-
Resolution: Done
-
Priority:
Highest
-
Affects Version/s: 3.4.0
-
AMRIT Sprint 48, AMRIT Sprint 49
-
Platform
-
UAT
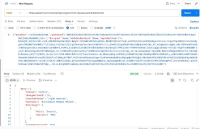
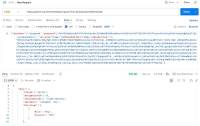
During VAPT (Vulnerability Assessment and Penetration Testing), it was discovered that access controls are not properly enforced on the https://uatamrit.piramalswasthya.org/tm-api/location/get/villageMasterFromBlockID/355, allowing unauthorized users to perform actions or access data beyond their intended privileges.
| Sr. No. |
Vulnerability Name | Vulnerable Point, Port or Parameter | CVE/CWE | CVSS Score | Overall Risk (Severity) |
Mapping with OWASP Testing Checklist | Observation / Description | Impact | Recommendation | Reference | Steps to reproduce |
| 1 | Broken Access Control | https://uatamrit.piramalswasthya.org/tm-api/location/get/villageMasterFromBlockID/355 | CWE-284 | 7.5 | High | OWASP Authorization Testing | This means that anyone, even unauthenticated users or external attackers, could access this endpoint and retrieve or interact with the data or functionality exposed by it. Such unrestricted access to sensitive or functional endpoints constitutes a broken access control vulnerability, allowing unauthorized data exposure or privilege escalation. | Unauthorized access to sensitive data or operations without credentials. Potential for data leakage, privacy violations, and security breach. Attackers could manipulate or tamper with resources without permission. |
Enforce strict authentication and authorization checks on all endpoints, especially those exposing sensitive data or critical functions. Audit endpoints for access control and verify that no publicly accessible endpoints provide unintended access. Implement role-based access control (RBAC) or attribute-based access control (ABAC) as appropriate. |
https://owasp.org/Top10/A01_2021-Broken_Access_Control/ | Step 1: During the security assessment, it was found that the endpoint block id/355 was publicly accessible without any authentication or authorization controls. |