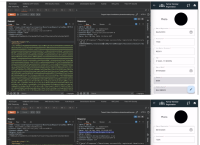
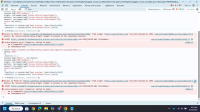
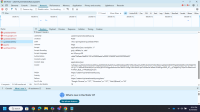
Vulnerability Name: CORS (Cross-Origin Resource Sharing) error
- Vulnerable Point:
https://amritdemo.piramalswasthya.org/tmapi-v1.0/registrar/registrarBeneficaryRegistrationNew - Observation / Description: Cross-Origin Resource Sharing (CORS) is an HTTP-header based mechanism that allows a server to indicate any other origins (domain, scheme, or port) than its own from which a browser should permit loading of resources. CORS also relies on a mechanism by which browsers make a “preflight” request to the server hosting the cross-origin resource, in order to check that the server will permit the actual request. In that preflight, the browser sends headers that indicate the HTTP method and headers that will be used in the actual request.
- Impact: The risk here is that a web client can put any value into the Origin request HTTP header in order to force web application to provide it the target resource content. In the case of a Browser web client, the header value is managed by the browser but another “web client” can be used (like Curl/Wget/Burp suite/…) to change/override the “Origin” header value. For this reason it is not recommended to use the Origin header to authenticate requests as coming from your site.
- Recommendation:
To mitigate the risk of CORS, we always recommend whitelisting your Access-Control-Allow-Origin instead of wildcarding. Using a wildcard prefix such as *.yoursite.com makes it more difficult for the attackers given they would need to find a vulnerability (such as cross-site scripting or cross-site request forgery) to issue the cross-origin request. However, it is frowned upon because it does not provide the critical need-to-know security control. With whitelisting, the scope of your Access-Control-Allow-Origin will be limited to only the sites that deal directly with your primary site or API and exclude any of your sites that do not. - Recommendation Solution:
CORS (Cross-Origin Resource Sharing) error occurs when a web application running in one domain (origin) tries to access resources from a different domain. This is a security mechanism implemented by web browsers to prevent unauthorized access to sensitive data.
When you are integrating with another system using an open API, the API server may be configured to only allow requests from specific domains or origins. If your application is not on the list of allowed origins, the API server will reject the request and return a CORS error.
To solve this issue, you need to configure your server to allow requests from the domain that your application is hosted on. This can be done by adding the appropriate CORS headers to the API response. Alternatively, you can use a proxy server to make the API request on behalf of your application, which will bypass the CORS restrictions.